Forums › Life › Computers, Gadgets & Technology › Computer Viruses, Trojans & Threats. › New Attack Can Deannonymize TOR Hidden Services.
this appears to be a variation on the techniques discovered by UK profs in the late 2000s (not long after TOR was first released) which were published and the experiments repeated across many science Universities in Northern Europe around the same time.
what is more surprising is many of these tech writers appear to have gone up to the same Universities; actually got their degrees rather than getting thrown out of the place for hacking their networks in a haze of drugs (and thus causing way more disruption than I even wanted to) and not all of them are that young either.
yet it seems they do not realise any electronic communications is always going to travel at or very near 299 792 458 m/s; and electronics in communication equipment will drift when the equipment changes temperature – such as when it is processing encrypted rather than clear traffic on top of any compression/optimisation algorithms used to squeeze more bandwidth out of a circuit.
This always has to be corrected for otherwise the comms link will start to act up and fail altogether.
if it is possible to generate any similar traffic via the comms links in the same areas of the entry and exit points it will therefore always be possible to locate its source or destination; whatever encrypt is used becomes irrelevant.
here are some examples on servers that are not even sending encrypted data. The first one is a telephone system in my roofspace; that regularly synchronises to NPL London to keep correct time.
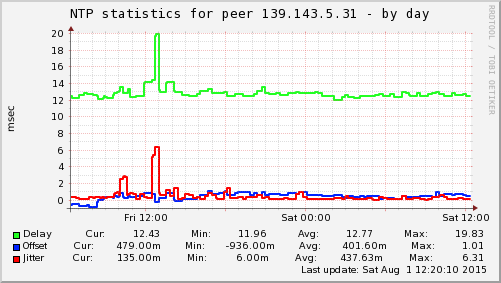
The lag/offset at Friday lunchtime appears to be from NPL London; it also happens at British “teatime”; maybe the boffins have connected their Teasmade to the atomic clock :laugh_at:
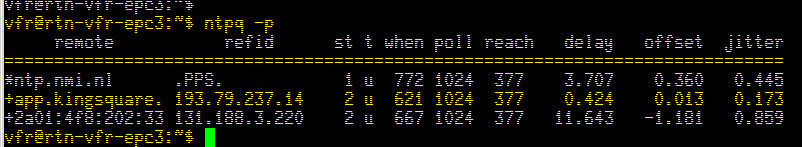
Now two from Nederland.
The first VPS runs an online radio station 24/7 and does some real time audio streaming which involves encoding the audio into a compressed format; as well as scheduling/playout. The software has some flaws and runs everything harder than it should (there is some “ruby on rails” or whatever they call it to make a pretty HTML5 display, which is a resources hog and goes badly wrong every so often).
NMI are the Netherlands Metrology Institute. They are cool enough to send me a pulse every second (you used to have to pay the KPN/PTT loads of Euros/Guilders to get a service like that!)
The second VPS mostlhy runs a helpdesk system which isn’t heavily used during the weekend (it does have another audio transcoder running in the background). they are the same power (CPU/RAM etc), running the same OS and in the same datacentre.
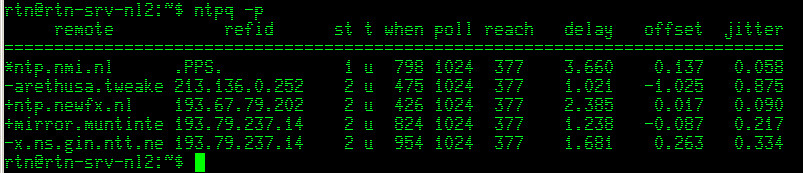
Note the difference in timing jitter across the two NL servers……
This sounds scary, but the onion network will be encrypted before this is able to become accomplished.
Some hacks don’t last forever.
No, this shows what you are visiting so you have no anonimity. They can’t read the traffic but they know its destination.
0
Voices
2
Replies
Tags
This topic has no tags
Forums › Life › Computers, Gadgets & Technology › Computer Viruses, Trojans & Threats. › New Attack Can Deannonymize TOR Hidden Services.